JWT Security refers to the security practices and protections applied when using JSON Web Tokens (JWT) for authentication and data exchange. JWT is a compact, stateless token used to verify user identity, and JWT security ensures the token cannot be tampered with, stolen, or misused. This is a critical component of modern web security.
Why JWT Security Is Important: Preventing JWT Attacks
JWT Security is important because the token often contains sensitive user information or access permissions, known as claims. If it is not secured properly, attackers can:
- Steal tokens from insecure storage.
- Modify the token data to escalate privileges (token tampering).
- Impersonate users.
- Access protected resources and APIs.
Good JWT security prevents these risks and ensures safe authentication and authorization.
How JSON Web Tokens (JWT) Work and the JWT Header
A JWT contains three parts: Header, Payload, and Signature. The three parts are base64-encoded and separated by dots: header.payload.signature.
The Role of the JWT Header and Signature Verification
- The Header (jwt header): This section specifies the signing algorithm (e.g., $\text{HS}256$ or $\text{RS}256$) and the type of token (JWT).
- The Payload (claims): This carries user data and authorization claims (e.g., user ID, roles, expiration time).
- The Signature (jwt signature): This is created by taking the encoded Header, the encoded Payload, and signing them with a secret key (for symmetric algorithms) or a private key (for asymmetric algorithms). The signature verifies that the token is valid and hasn’t been tampered with.
To ensure security, the signature must be protected and properly verified. This process is called signature verification.
Key Components of JWT Security: Secret Key and Signature Verification
Strong Secret Key and Private Key Management
Using a strong secret (or a private key in asymmetric encryption) is fundamental. This key prevents attackers from forging valid JWTS. If an attacker knows your secret key, they can generate a fraudulent JWT signature and successfully launch attacks. For RS256 and similar algorithms, the recipient uses a matching public key for signature verification.
Signature Verification: The Core Security Check
Servers must perform signature verification on every incoming token before trusting its claims. This check confirms that the token was genuinely issued by the server and that the payload hasn’t been altered.
Proper Token Expiration and Token Revocation
Short-lifespan tokens reduce the risk of misuse if stolen. Additionally, in scenarios where a token must be immediately invalidated (e.g., a user logs out), implementing a secure token revocation mechanism is essential, even though JWT is designed to be stateless.
HTTPS Mandatory for Secure Transmission
Tokens must always be sent over HTTPS (or $\text{TLS}$) to avoid interception by man-in-the-middle attacks. This is a non-negotiable step in web security.
Secure Token Storage
Tokens should be stored in secure places like HttpOnly cookies, not localStorage.
Common JWT Security Threats and Algorithm Confusion
JWT Attacks and $\text{Algorithm}$ Confusion
A major class of JWT attacks involves exploiting weaknesses in the verification process:
- Token Theft: Attackers may steal tokens from insecure storage.
- Replay Attacks: Using a valid token again after it should no longer be valid.
- Signature Forgery: Weak secrets or keys can allow hackers to generate fake tokens.
- Token Tampering: Modifying payload data to escalate privileges.
- Algorithm Confusion: This critical type of JWT attack occurs when an attacker modifies the $\text{alg}$ parameter in the JWT Header from an asymmetric algorithm (like $\text{RS}256$) to a symmetric one (like $\text{HS}256$). The server, expecting an $\text{RS}256$ token and having the associated $\text{public key}$, might mistakenly use this $\text{public key}$ as the secret key for the $\text{HS}256$ verification. The attacker, knowing the server’s public key, can then forge a valid $\text{HS}256$ signature.
Best Practices for JWT Security
To secure your API and protect your users, follow these best practices for JWT management:
- Always use HTTPS for all communication.
- Use strong signing algorithms like $\text{RS}256$ and properly manage the private key.
- Set short token expiration times (e.g., 15–30 minutes) and use refresh tokens securely.
- Rotate keys regularly.
- Validate tokens on every request using robust signature verification.
- Avoid storing tokens in localStorage.
- Never store highly sensitive data inside the JWT payload.
- Properly implement token revocation mechanisms where needed.
- Use libraries that strictly check the $\text{alg}$ field in the header to prevent algorithm confusion attacks.
- JWT is often used in OAuth $2.0$ and OpenID Connect flows for secure authorization.
Benefits of Strong JWT Security
Strong JWT Security offers numerous advantages for modern applications:
- Protects user accounts and personal data.
- Prevents unauthorized access to API resources.
- Keeps API communication safe and trusted.
- Improves overall application security.
- Supports scalable authentication for web and mobile apps.
Final Thoughts
JWT Security plays an essential role in modern web security and authentication systems. By following best practices—especially regarding strong secret key management, rigorous signature verification, and mitigating JWT attacks like algorithm confusion—you can ensure that your JWTS remain safe, valid, and trusted across your applications.
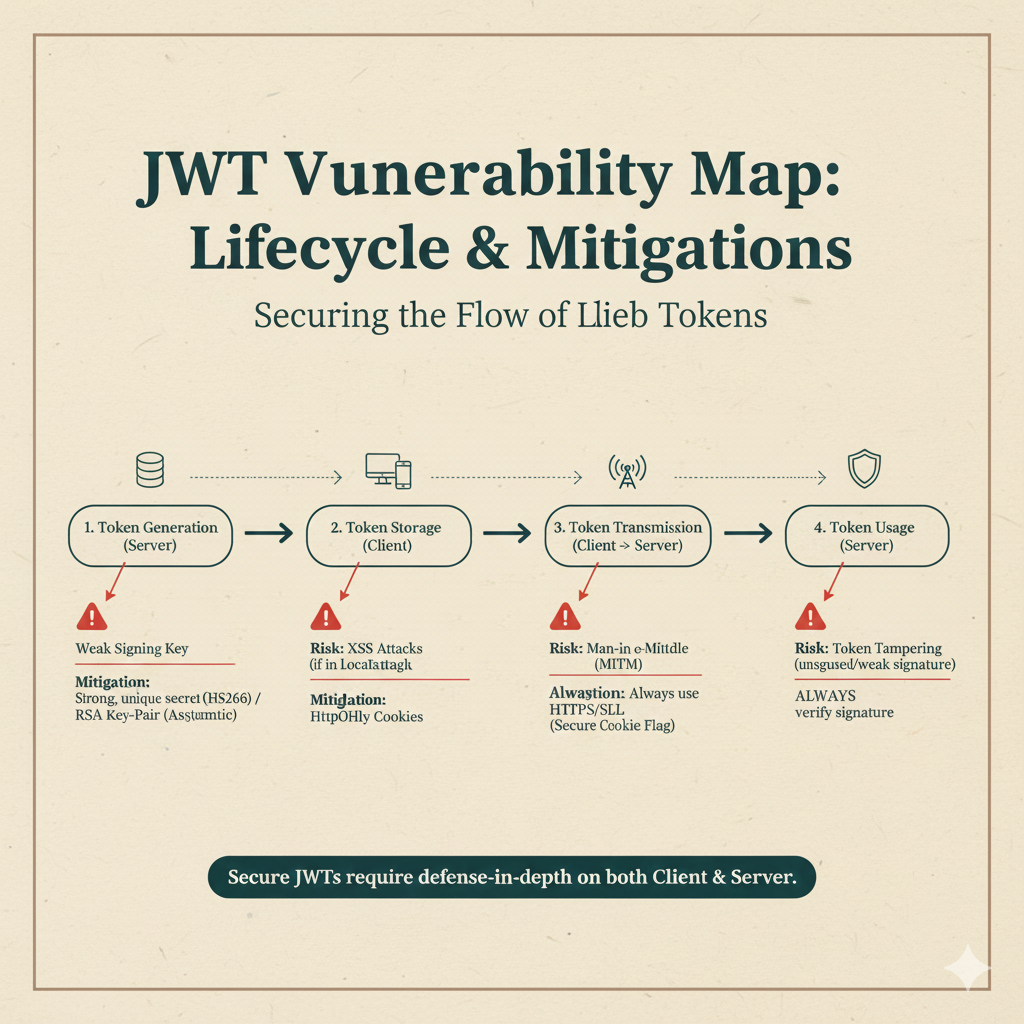
JWT Vulnerability Map: Lifecycle & Mitigations
The infographic you provided illustrates the critical security risks associated with JSON Web Tokens (JWTs) at each stage of their lifecycle, along with the essential mitigation strategies required for a defense-in-depth approach.
1. Token Generation (Server)
- Risk: Weak Signing Key. If the secret used to sign the token is too short, common, or predictable, an attacker can easily crack the key and forge valid tokens (e.g., using rainbow tables or dictionary attacks).
- Mitigation: Use a strong, unique secret (for HS256) or a secure RSA/EC Key-Pair (for asymmetric signing algorithms like RS256).
2. Token Storage (Client)
- Risk: XSS Attacks (if stored in
localStorage). Client-side storage likelocalStorageis accessible by any script running on the page. If your site has a Cross-Site Scripting (XSS) vulnerability, an attacker can steal the token and impersonate the user. - Mitigation: Store the token in
HttpOnlyCookies. This prevents client-side JavaScript from accessing the token, providing robust protection against XSS token theft.
3. Token Transmission (Client $\rightarrow$ Server)
- Risk: Man-in-the-Middle (MITM) Attack. If the token is sent over an unencrypted network (plain HTTP), an attacker can intercept and read the token, leading to session hijacking.
- Mitigation: ALWAYS use HTTPS/SSL/TLS. Furthermore, enforce the
SecureCookie Flag when setting the token cookie, ensuring the browser only transmits the cookie over a secure, encrypted connection.
4. Token Usage (Server)
- Risk: Token Tampering (Unsigned/Weak Signature). If the token signature is not verified, or if the token uses the insecure
alg: "none"algorithm, an attacker can alter the payload claims (e.g., changing roles or permissions) without detection. - Mitigation: ALWAYS verify the signature on the server side using the corresponding secret or public key. This is the most crucial step for ensuring the token’s integrity.
Leave a Reply