JSON Web Tokens (JWT) have become a cornerstone in modern web application security, providing a compact, URL-safe means of representing claims between two parties. If you’re looking to understand and implement secure authentication, mastering “How to use JWT” is essential. This guide will walk you through the fundamentals, implementation, and best practices for leveraging JWTs effectively.
What is JWT (JSON Web Token)?
A JWT is an open standard (RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed. JWTs are commonly used for authorization, where a server can verify a user’s identity based on the token.
JWT Structure: Header, Payload, and Signature
Every JWT consists of three parts, separated by dots (.), which are Base64Url-encoded:
- Header: Typically consists of two parts: the type of the token, which is JWT, and the signing algorithm being used, such as HMAC SHA256 or RSA.
{
"alg": "HS256",
"typ": "JWT"
} - Payload: Contains the claims. Claims are statements about an entity (typically, the user) and additional data. There are three types of claims: registered, public, and private claims.
{
"sub": "1234567890",
"name": "John Doe",
"iat": 1516239022
} - Signature: To create the signature part, you take the encoded header, the encoded payload, a secret, the algorithm specified in the header, and sign that. The signature is used to verify that the sender of the JWT is who it says it is and to ensure that the message hasn’t been tampered with.
HMACSHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),
secret
)
The resulting JWT looks like this:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5cWhy Use JWT for Authentication?
JWTs offer several compelling advantages for authentication and authorization:
- Statelessness: With JWTs, the server doesn’t need to store session information. Each request contains the necessary authentication data, making it ideal for scalable, distributed systems and microservices.
- Compact: JWTs are small in size, allowing them to be sent through URL, POST parameter, or inside an HTTP header. This also means faster transmission.
- Self-contained: The payload contains all the necessary user information, reducing the need for database lookups on every request, thereby improving performance.
- Security: Signed JWTs ensure that the claims cannot be altered after the token has been issued, providing a robust security mechanism against tampering.
How to Implement JWT: A Step-by-Step Overview
Implementing JWT involves a few key steps:
1. User Authentication and Token Generation
When a user successfully logs in (e.g., provides correct username/password), your server generates a JWT. This involves:
- Creating a header (algorithm, type).
- Creating a payload (user ID, roles, expiry time, etc.).
- Signing the header and payload with a secret key to produce the signature.
The server then sends this JWT back to the client.
2. Client-Side Storage and Transmission
The client (e.g., a web browser or mobile app) receives the JWT and typically stores it in local storage, session storage, or as an HTTP-only cookie. For subsequent requests to protected routes, the client includes the JWT, usually in the Authorization header as a Bearer token.
Authorization: Bearer <your_jwt_token>3. Server-Side Token Verification
Upon receiving a request with a JWT, the server performs the following:
- Decodes the header and payload.
- Verifies the signature using the same secret key used for signing. If the signature is invalid, the token has been tampered with or is from an unauthorized source.
- Checks the token’s claims, such as expiration time (
exp) and issuer (iss).
If all checks pass, the server trusts the token and grants access to the requested resource based on the claims.
JWT Best Practices for Enhanced Security
- Keep Your Secret Key Secure: Never expose your secret key. It’s crucial for signing and verifying tokens.
- Set Expiration Times (
expclaim): Tokens should have short expiration times to limit the window of opportunity for attackers if a token is compromised. - Implement Token Revocation: While JWTs are stateless, you might need mechanisms to revoke tokens prematurely (e.g., on logout or password change) using a blacklist.
- Use HTTPS: Always transmit JWTs over HTTPS to prevent eavesdropping and Man-in-the-Middle attacks.
- Avoid Storing Sensitive Data in Payload: The payload is encoded, not encrypted. Do not put highly sensitive, confidential information directly into the payload.
- Use Strong Signing Algorithms: Prefer algorithms like HS256 (HMAC with SHA-256) or RS256 (RSA with SHA-256).
Conclusion
JWTs provide a powerful and flexible solution for secure, stateless authentication in modern applications. By understanding their structure, how they work, and implementing best practices, you can significantly enhance the security and scalability of your web services. Embrace JWTs to build robust and efficient authentication systems.
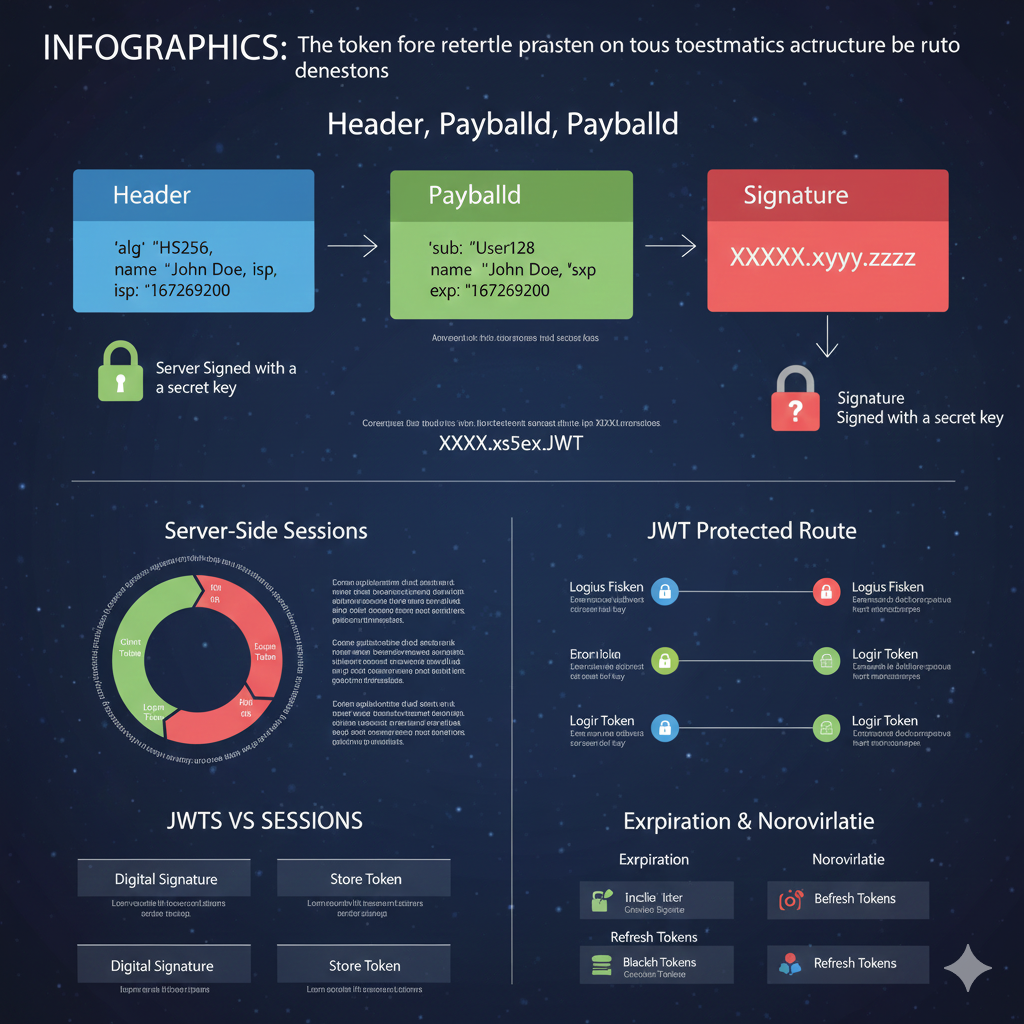
The image is an infographic titled “INFOGRAPHICS: The token fore retertle praistens on tous toestmatics actructure be ruto denestons”. It is a highly technical visualization that breaks down the JSON Web Token (JWT) structure, its use in protected routes, and its comparison to traditional server-side sessions.
🧱 The Structure of a JWT
The top section illustrates the three distinct parts of a JWT:
- Header (Blue): Contains metadata about the token.
- Example:
"alg": "HS256","typ": "JWT",isp: "167269200". - Security: This section is Server Signed with a secret key.
- Example:
- Payload (Green): Contains the claims (user data and metadata).
- Example:
"sub": "User128",name: "John Doe",exp: "167269200". - Note: This data is base64 encoded, not encrypted, meaning it is readable by the client.
- Example:
- Signature (Red): Used by the server to verify the token’s integrity.
- Security: This section is Signed with a secret key.
- Verification: If the signature does not match, the token is rejected as tampered with.
- Combined Format: The final JWT is the concatenation of these three parts:
Header.Payload.Signature(e.g.,XXXXX.XXXX.ZZZZ).
🛡️ JWTs vs. Sessions (Server-Side Sessions)
A diagram compares the JWT approach to traditional session management:
- JWT Security: Based on the Digital Signature.
- Session Security: Based on the Store Token (lookup in a server-side storage like a database or Redis).
- A pie chart implies that JWTs offer a high level of security and scalability due to being stateless, while sessions require constant server interaction.
🔒 JWT Protected Route Flow
This section shows how the token is used to access secure API endpoints:
- Logius Fisken (Protected Route): Access requires a valid token.
- Logir Token: If the token is valid, access is granted.
⏳ Expiration & Revocation
This section addresses two key security challenges with JWTs:
- Expiration: Uses short-lived Access Tokens and longer-lived Refresh Tokens to manage session duration.
- Noroviriatie (Revocation): Involves using a mechanism like a Blacklist or Refresh Tokens (managed by a store like Redis) to instantly invalidate tokens before they naturally expire.
learn for more knowledge
Json parser -> BeautifulSoup JSON Parser-Combining BeautifulSoup and JSON for Web Scraping – json parse
Mykeywordrank-> SEO: Your Comprehensive Guide to Boosting Search Engine Optimization Rankings – keyword rank checker
Json Compare ->JSON Comparator: The Ultimate Guide to JSON Compare Online and Offline Tools – online json comparator
Fake Json –>What Is JSON Mock API? (Beginner-Friendly Explanation) – fake api
Leave a Reply