Okta JWT refers to a JSON Web Token (JWT) that is created, signed, and verified by Okta, a popular identity and authentication platform. Okta uses JWTs (or tokens) to securely manage user login, API authorization, and access control in modern web applications.
A JWT is a small, encoded token that contains user identity and permission information (known as claims). When generated by Okta, it becomes a trusted token that applications can validate to confirm whether a user is authenticated.
Why Okta Uses JSON Web Token for JWT Authentication
Okta leverages the stateless and secure nature of the JSON Web Token standard for robust JWT authentication and security:
- Secure user authentication: Providing a verifiable identity token.
- Authorizing access to API s and resources.
- Single Sign-On SSO across multiple web applications.
- Identity management and providing various jwt claims (e.g., user roles).
- Protecting backend services by requiring a valid JWT token for access.
What an Okta JWT Contains: Understanding JWT Claims and Types
An Okta JWT is a single token that can be one of several jwt types (e.g., ID Token or Access Token, each serving a different purpose in authentication and authorization). Regardless of the type, every JWT contains verifiable information, known as claims:
- Issuer (iss): Always identifies Okta as the origin.
- Subject (sub): The unique User ID.
- Audience (aud): The client ID or API that the token is intended for.
- Expiration (exp): The token validation time.
- Custom claims: Permissions, roles, email, or other data added by the Okta developer during configuration.
How Okta JWT Works: Signature Verification and Signing Keys
The security of the Okta JWT relies entirely on the jwt signature, which ensures the token hasn’t been tampered with.
1. Okta Generates a JWT Signature
- User Logs In: The user successfully authenticates through Okta.
- Okta Generates a JWT: Okta creates the token (Header, Payload, Signature) and signs it using its private key. The Header specifies the signing algorithm (e.g., RS256).
2. Token Validation via Signing Keys
- Application Receives the Token: The application receives the JWT token.
- Token Is Verified: The application verifies the jwt signature using Okta’s public key (which is publicly available via a standard endpoint).
- This process uses the public key to check if the signature was genuinely created by the matching private key (signing keys) held by Okta. This is the core of token validation.
- User Gets Access: If the validation passes, the user is granted secure access to protected resources.
Benefits of Using Okta JWT
Leveraging Okta for your JWT authentication provides significant advantages for your web application and API security:
- High-level security backed by Okta‘s robust infrastructure.
- Easy integration with API using the standard JWT format.
- Seamless compatibility with OAuth 2.0 and OpenID Connect flows.
- Reduces the need for building and managing custom authentication systems.
- Scalable for enterprise-level apps and large numbers of clients and tokens.
Final Summary
The Okta JWT is a standardized, secure authentication token generated and verified by Okta. It serves as the cornerstone of JWT authentication in modern systems, enabling web applications to reliably confirm user identity, manage jwt claims, and protect API using strong security practices like private key signing and public key token validation.
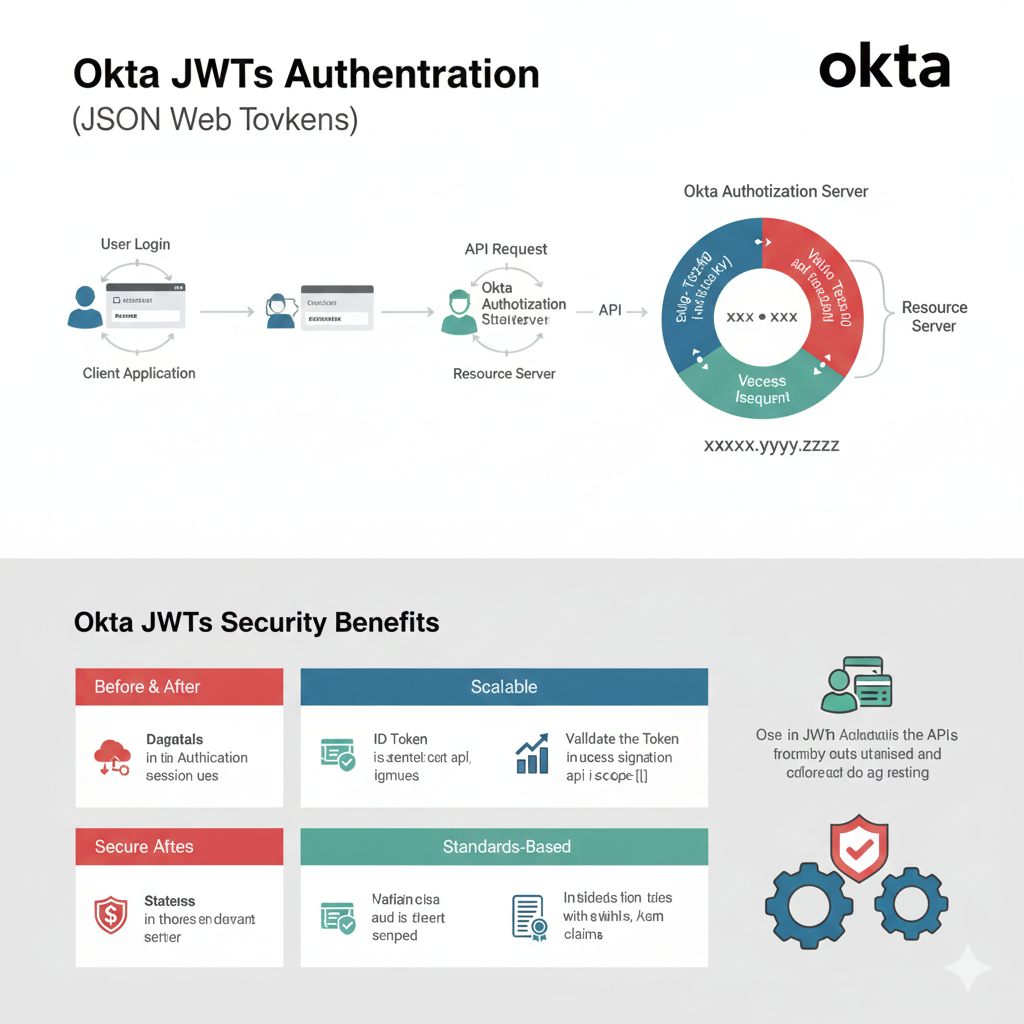
“Okta JWTs Authentication (JSON Web Tokens)” Infographic
This infographic explains the authentication flow using JSON Web Tokens (JWTs) facilitated by the Okta Authorization Server, and details the security benefits of using Okta JWTs.
1. Authentication Flow (User Login to Resource Server)
This section illustrates the typical sequence of events when a user attempts to access a protected resource.
| Step | Component | Action | Details |
| Start | User Login | The user inputs credentials into the Client Application. | The client sends credentials (e.g., username/password) to a secured endpoint. |
| Exchange | Okta Authorization Server | Okta verifies the credentials and issues a token. | The token contains a Header, Payload, and Signature. |
| Access | API Request | The client application attaches the JWT (access token) to the API request. | The request goes to the Resource Server. |
| Validation | Resource Server | The server validates the token’s signature using Okta’s public keys. | The circular diagram shows the validation process (e.g., Value Texznd and Value Teczon segments). |
| Result | Resource Server | Grants Vececss Iseeuent (Successful Access). | The server returns the requested resource. |
2. Okta JWTs Security Benefits
This section highlights the key advantages of using JWTs, particularly when integrated with Okta.
| Category | Benefit | Description |
| Before & After | Dagatais | Improves authentication session use. |
Secure Aftecs | Stateless | Improves security and simplifies deployment. |
| Scalable | ID Token | The token is self-contained and signed. |
| Scalable | Validation | Validates the token and its access scope. |
| Standards-Based | Standard | Uses standard claims for authentication and audit. |
| Standards-Based | Claims | Provides evidence with events, and key claims. |
| General Use | APIs & AD | Used in APIs, Active Directory, and federated identity management. |
learn for more knowledge
Json Parser ->APIDevTools JSON Schema Ref Parser: Resolving JSON Schema References – json parse
mykeywordrank->Google Search Engine Optimization (SEO)-The Key to Higher Rankings – keyword rank checker
Json Compare ->Online JSON Comparator, JSON Compare tool – online json comparator
Fake Json ->Fake API: Why Fake JSON APIs Are Useful for Developers – fake api
Leave a Reply